tl;dr: ElGamal public key encrypting $\approx$ Using an ephemeral Diffie-Hellman exchanged key as a one-time pad.
Preliminaries
- We assume a group $\Gr$ where Decisional Diffie-Hellman (DDH) is hard
- We use additive group notation for $\Gr$
Exponentiated ElGamal
This variant of ElGamal (first proposed by Cramer, Gennaro and Schoenmakers1?) encrypts a field element $m\in\F$ by “exponentiating” it into $m\cdot G$. The encryption pubkey is $\ek \bydef \dk \cdot H$, where $H$ is another generator such that $\log_G{H}$ is unknown and hard to compute.
Note that the original ElGamal paper is described as only encrypting group element messages $m\in \Gr$. As a result, it only needs one generator $H$.
$\mathsf{E}.\mathsf{KGen}(1^\lambda) \rightarrow (\mathsf{dk}, \mathsf{ek})$
- $\dk \randget \F$
- $\ek \gets \dk \cdot H$
$\mathsf{E}.\mathsf{Enc}(\mathsf{ek}, m; r) \rightarrow (C, D)$
- $C \gets m \cdot G + r\cdot \ek$
- $D \gets r \cdot H$
$\mathsf{E}.\mathsf{Dec}(\mathsf{dk}, (C,D)) \rightarrow m\cdot G$
- return $C - \dk \cdot D$
Correctness
Correctness holds because:
\begin{align}
C - \dk \cdot D
&= (m \cdot G + r\cdot \ek) - \dk\cdot(r\cdot H)\\
&= (m \cdot G + (r\cdot \dk) \cdot H) - (\dk\cdot r)\cdot H\\
&= m\cdot G
\end{align}
Twisted ElGamal
I believe this was first proposed by Chen et al.2?
This variant of ElGamal adds a small twist: the $r \cdot G $ and $r\cdot \ek$ components from exponentiated ElGamal are switched out.
The advantage is that the first component of the ciphertext (i.e. , $C$ from above) can now be treated as a Pedersen commitment to the encrypted message $m$.
This has efficiency advantages when composing Twisted ElGamal with $\Sigma$-protocols and other ZK proof systems like Bulletproofs3.
$\mathsf{E}.\mathsf{KGen}(1^\lambda) \rightarrow (\mathsf{dk}, \mathsf{ek})$
- $\dk \randget \F$
- $\ek \gets \dk^{-1} \cdot H$
$\mathsf{E}.\mathsf{Enc}(\mathsf{ek}, m; r) \rightarrow (C, D)$
- $C \gets m \cdot G + r\cdot H$
- $D \gets r \cdot \ek$
$\mathsf{E}.\mathsf{Dec}(\mathsf{dk}, (C,D)) \rightarrow m\cdot G$
- return $C - \dk \cdot D$
Correctness
Correctness holds because:
\begin{align}
C - \dk \cdot D
&= (m \cdot G + r\cdot H) - \dk\cdot(r\cdot \ek)\\
&= (m \cdot G + r \cdot H) - (\dk\cdot r\cdot\dk^{-1}) H\\
&= (m \cdot G + r \cdot H) - r\cdot H\\
&= m\cdot G
\end{align}
Conclusion
Threshold variant. Weighted variant. DLog algorithms.
Appendix
Original ElGamal
The original ElGamal encryption paper4 talks about encrypting a group element $m \in \Gr$, where $\Gr =\Zp$ and $p=kq+1$ for some other large prime $q$. (These days, $q \approx 2^{3072}$.)
First, the paper recalls the Diffie-Hellman5 key exchange:
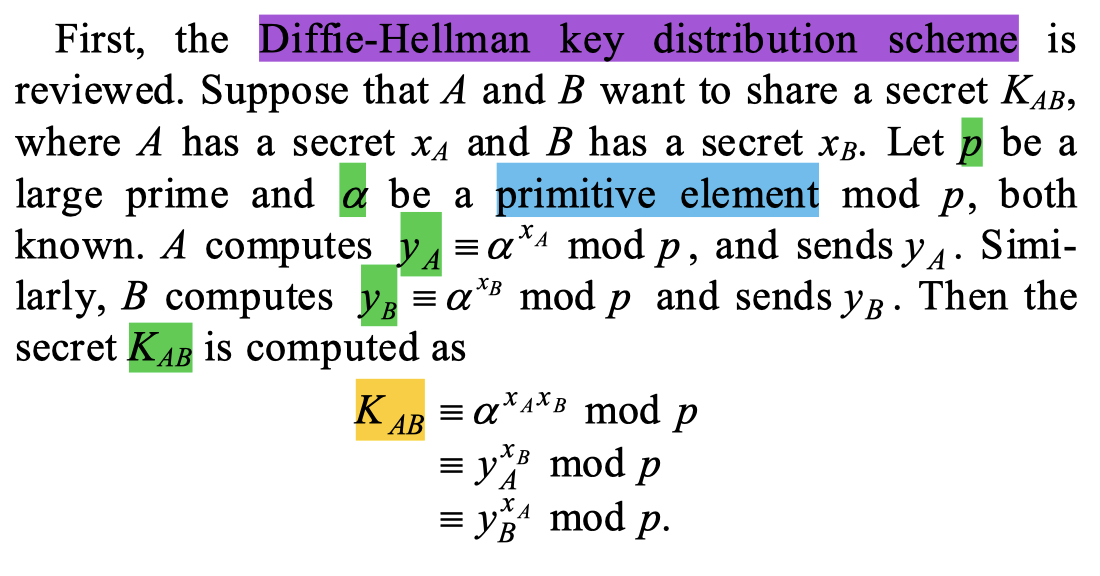
Then, it emphasizes that the prime $p$ should have a large prime factor (i.e., our $q$ above):

Lastly, it introduces the scheme by describing how to encrypt and decrypt a group element in $m\in\Gr$:
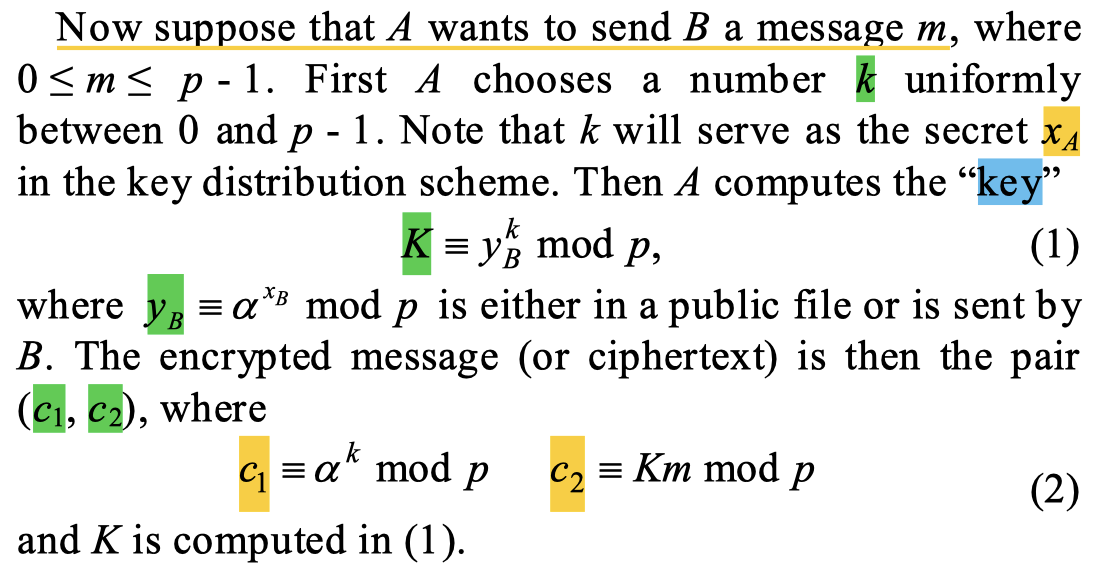
Great were the days when the main result of a cryptography paper could be stated in three paragraphs like this! 🥲
References
For cited works, see below 👇👇
-
A Secure and Optimally Efficient Multi-Authority Election Scheme, by Cramer, Ronald and Gennaro, Rosario and Schoenmakers, Berry, in Advances in Cryptology — EUROCRYPT ‘97, 1997 ↩
-
PGC: Decentralized Confidential Payment System with Auditability, by Chen, Yu and Ma, Xuecheng and Tang, Cong and Au, Man Ho, in Computer Security – ESORICS 2020, 2020 ↩
-
Bulletproofs: Short Proofs for Confidential Transactions and More, by B. Bünz and J. Bootle and D. Boneh and A. Poelstra and P. Wuille and G. Maxwell, in 2018 IEEE Symposium on Security and Privacy (SP), 2018 ↩
-
A public key cryptosystem and a signature scheme based on discrete logarithms, by Elgamal, T., in IEEE Transactions on Information Theory, 1985 ↩
-
New Directions in Cryptography, by Diffie, W. and Hellman, M., in IEEE Trans. Inf. Theor., 2006, [URL] ↩